How do you accelerate from identity chaos to complete control?
Unify your entire identity attack surface—human and non-human—in a single intelligent platform. Axiad Mesh delivers the Identity Visibility and Intelligence your IAM stack never could.
What is an Identity Visibility and Intelligence Platform (IVIP)?
The missing layer in your IAM stack that transforms fragmented identity data into unified intelligence.
Axiad Mesh: Leading the IVIP Revolution
While industry analysts just defined IVIP as a category, Axiad has been pioneering IVIP capabilities for some time. We saw the visibility gap long before it had a name—and built the platform to solve it. Today, Axiad Mesh stands as the first true IVIP, purpose-built to unify your identity fabric and accelerate your security posture from reactive to proactive.
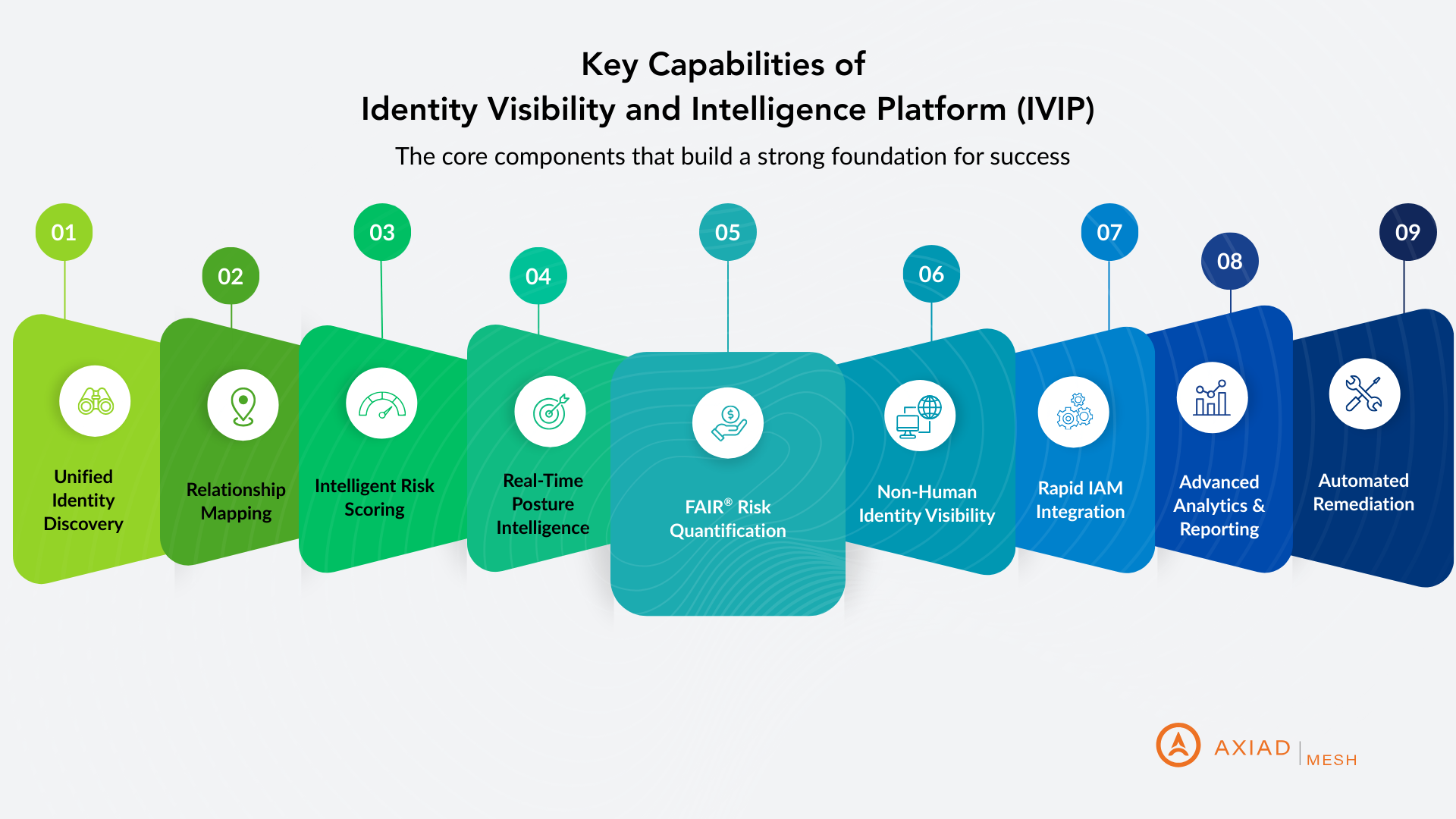
What are key IVIP capabilities?
- Unified Identity Discovery
- Automatically discover and catalog every identity across your enterprise—from Active Directory and Azure AD to AWS, GCP, SaaS platforms, and on-premises systems. See humans, service accounts, API keys, certificates, and AI agents in one unified view.
- Relationship Mapping
- Map the complex web of identity relationships and dependencies across your entire environment. Understand how identities chain together, expose hidden privilege paths, and visualize your complete identity fabric—not just isolated accounts.
- Intelligent Risk Scoring
- AI-powered analytics continuously assess identity risk based on permissions, behavior, access patterns, and toxic combinations. Prioritize remediation efforts with quantifiable risk scores that speak to both technical and business stakeholders.
- Real-Time Posture Intelligence
- Monitor identity configuration and security posture in real-time across all IAM controls. Detect drift, misconfigurations, and policy violations the moment they occur—not weeks later during an audit.
- Non-Human Identity Visibility
- Finally gain control over the identity explosion: service accounts, API keys, OAuth tokens, certificates, cloud roles, and AI agents. Track their lifecycle, usage, and blast radius across your entire environment.
- Rapid IAM Integration
- Connect your existing asset management and IAM stacks—CMDB, HRMS, IGA, PAM, CIEM, directories, and SaaS apps—in days, not months. Normalize data across disparate systems and break down identity silos without replacing what already works.
- Advanced Analytics & Reporting
- Transform raw identity data into executive-ready insights with risk scores and financial risk analysis. Generate compliance reports, demonstrate security improvements, and answer board-level questions with confidence using data-driven intelligence.
- Automated Remediation
- Don't just identify risks—fix them. Trigger automated workflows, orchestrate access reviews, and remediate toxic permissions directly through your existing IAM controls with enriched data from your IVIP. Intelligence that drives action.
- FAIR® Risk Quantification
- Translate identity risk into financial terms executives understand. Leverage FAIR (Factor Analysis of Information Risk) methodology to automatically quantify probable loss exposure, calculate risk in dollar amounts, and demonstrate ROI on identity security investments with board-ready financial reports.
What are the use cases for IVIP?
From Zero Trust to AI security, IVIP powers the identity programs that matter most. These are common use cases for IVIP:
- Zero Trust Implementation
Achieve continuous verification at scale. Map every identity's effective permissions across your estate and enforce least-privilege access in real-time. Turn "never trust, always verify" from aspiration to reality. - Identity Attack Surface Reduction
Shrink your exposure by identifying and eliminating over-privileged accounts, dormant credentials, toxic permission combinations, and shadow identities hiding in your environment. - Non-Human Identity Governance
Take control of the identity explosion. Discover every service account, API key, certificate, and cloud role. Track ownership, monitor usage, rotate credentials, and prevent the next supply chain compromise. - Intelligent Access Reviews
Transform access reviews from compliance theater to risk reduction. Automatically scope reviews based on risk, provide reviewers with context they need, and track remediation to completion. - Cloud IAM Optimization
Unify visibility across multi-cloud environments. Detect overly permissive cloud roles, unused IAM policies, and cross-account risks before they become breaches. - Threat Detection & Response
Correlate identity intelligence with security events. Detect privilege escalation and anomalous access patterns. - Compliance Readiness
Demonstrate compliance with SOC 2, ISO 27001, PCI DSS, and regulatory requirements. Generate audit-ready reports showing who has access to what, when access was granted, and by whom. - AI Agent Security
Secure the AI revolution. Track AI agents, monitor their access patterns, enforce guardrails, and ensure AI identities follow the same governance as human users—without slowing innovation. - M&A Integration
Rapidly assess identity risk during acquisitions. Discover all identities, map entitlements, identify toxic combinations, and integrate identity governance across merged environments in weeks. - Executive Risk Reporting
Answer the board's toughest questions with confidence. Quantify identity risk in financial terms, demonstrate security improvements over time, and prove ROI on your IAM investments. - IGA Enhancement
Supercharge your existing IGA investment. Fill visibility gaps, enrich governance workflows with risk intelligence, and extend IGA coverage to systems it can't reach natively. - Credential Sprawl Control
Discover certificate sprawl, orphaned API keys, and forgotten credentials across your environment. Track expiration dates, monitor usage, and automate rotation before certificates cause outages. - Post-Quantum Cryptography (PQC) Readiness
Prepare for the quantum threat before it arrives. Discover every certificate and cryptographic key in your environment, identify quantum-vulnerable algorithms (RSA, ECC), assess migration readiness, and build your crypto-agility roadmap to PQC standards.
Why does Axiad Mesh lead the IVIP category?
We didn't pivot to IVIP when the analysts defined the category. We pioneered the capabilities that define the category.
- First to Market
- While competitors are scrambling to add IVIP features, we've already been delivering unified identity intelligence. Our customers already have the visibility advantage analysts say will take others years to achieve.
- Purpose-Built, Not Bolt-On
- Axiad Mesh was architected from day one as an intelligence layer. We're not an IGA, ITDR, or ISPM tool with dashboards added—we're a true IVIP that makes every other IAM tool in your stack more effective.
- PKI Intelligence Built-In
- As a leader in PKI credential management, we bring unique certificate and cryptographic visibility that other IVIPs lack. Discover every crypto asset, track who owns those assets, and prepare for post-quantum cryptography—all from one platform.
- Deployment at Scale
- Start seeing value in days, not months. Our deployment methodology accelerates time-to-value and ensures adoption success.
- Integrate, Don’t Rip and Replace
- Native integrations with the tools you already use. We don't replace your stack—we unify it, normalize it, and make it intelligent. Work with your existing investments, not against them.
Get Your Complimentary FAIR® Identity Risk Analysis
LIMITED TIME OFFER
See your identity risk quantified in financial terms. Axiad Mesh will analyze your environment and deliver a comprehensive FAIR assessment showing probable loss exposure, risk prioritization, and investment recommendations—at no cost.
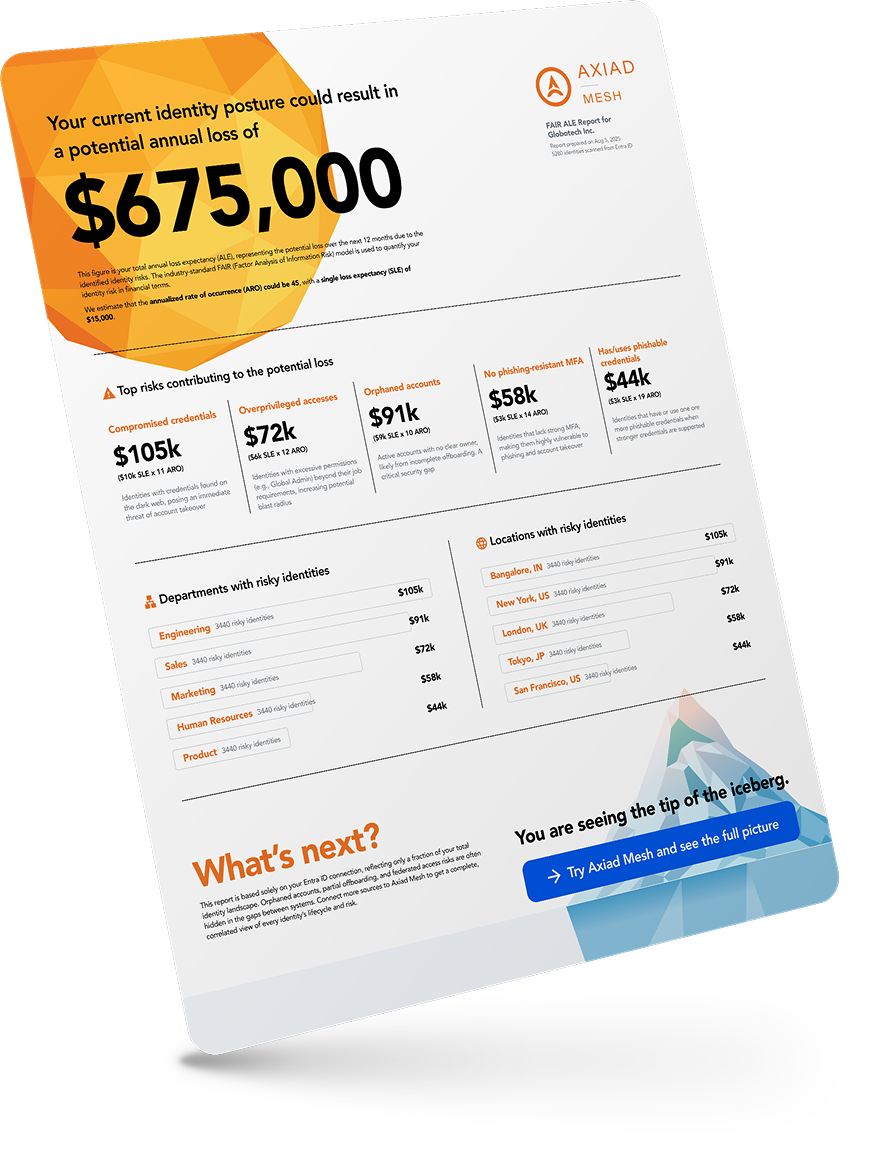
Your Free Report Includes:
- Financial Risk Quantification - Probable annual loss exposure in dollar amounts
- Risk Prioritization - Top identity risks ranked by financial impact
- ROI Projections - Expected returns on identity security investments
Request Your Free FAIR® Analysis Today
No software purchase required, and completely confidential!*
*Trusted by federal agencies and Fortune 500 enterprises to secure their identity fabric


























%201.avif)







