NIST, CISA, and Gartner Experts Say Quantum Will Break Today’s Encryption by 2029—Here's How Axiad Mesh Accelerates PQC Readiness
The clock is ticking. For organizations still wondering if post-quantum cryptography (PQC) migration is urgent, guidance is unequivocal: the time to prepare is now. According to the “Begin Transitioning to Post-Quantum Cryptography Now” article by Mark Horvath, Gartner®, “Quantum computing will render traditional cryptography unsafe by 2029."
But here's the challenge: most organizations don't even know all cryptography they're using, where it's deployed, or which systems depend on vulnerable algorithms.
Axiad Mesh, built for Identity Visibility and Intelligence, solves the cryptographic discovery challenge that lies at the heart of PQC readiness.
How Urgent is the Quantum Threat to Cryptography?
Industry experts warn that the danger isn't waiting until 2029. Security leaders must anticipate attacks where adversaries collect encrypted data today and store it for future decryption once quantum computers become available. This means that sensitive data encrypted with current algorithms—even if it seems secure today—may be compromised tomorrow.
The scope of the problem is staggering. Asymmetric cryptography powers virtually every aspect of modern security: X.509 certificates, digital signatures, SSH keys, TLS/SSL connections, VPNs, code signing, identity and access management systems, and countless other critical functions. Unlike cryptographic hash functions that get updated relatively frequently, RSA and elliptic curve cryptography have been the foundation of digital security for over thirty years. Replacing them across an entire enterprise isn't a simple software patch, it's a fundamental transformation.
What is a Framework for Post Quantum Cryptography Migration?
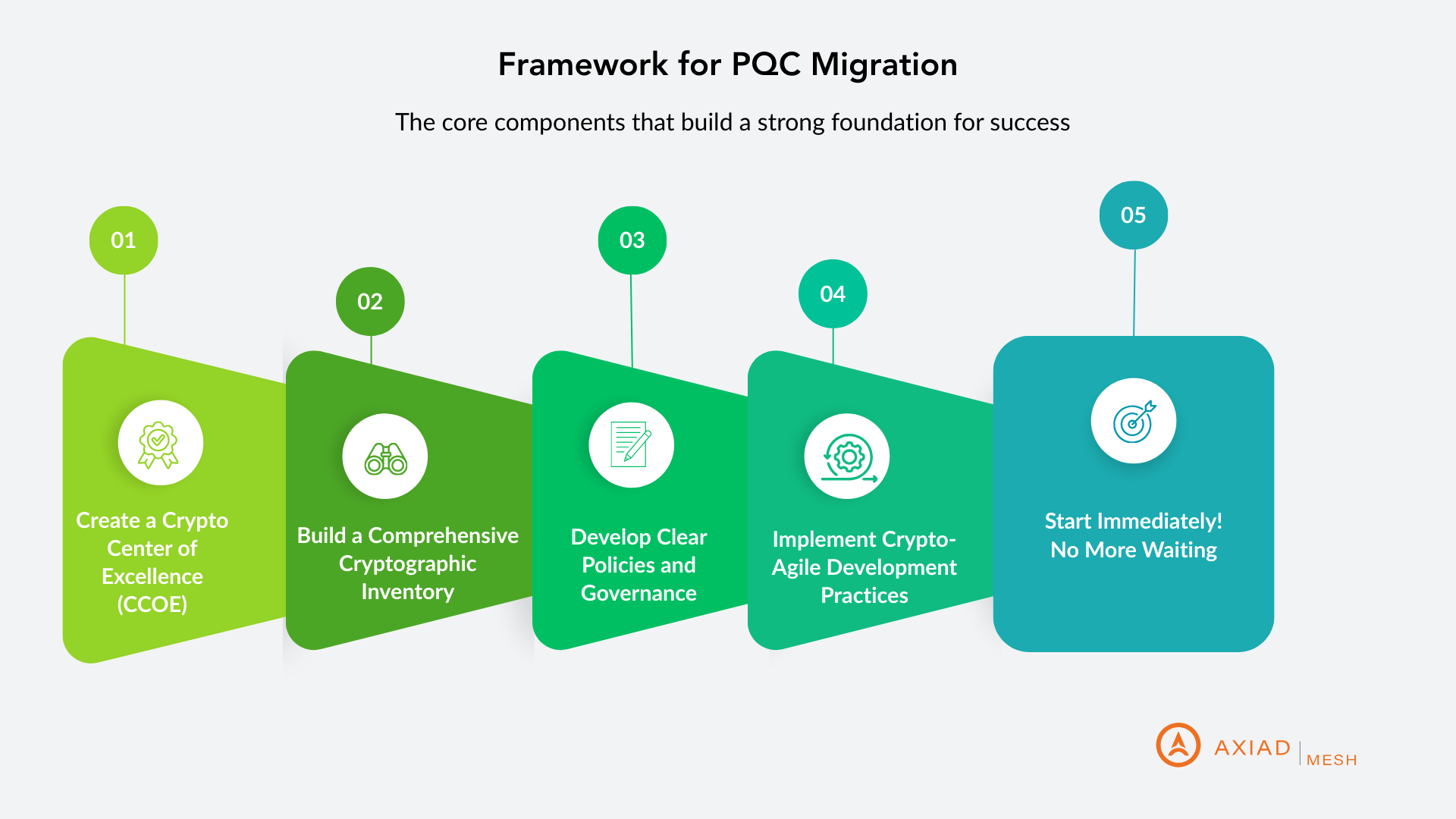
Reports from Gartner, CISA, and NIST provide clear, actionable guidance for organizations preparing for the post-quantum era. Their recommendations can be distilled into five critical imperatives:
1. Create a Crypto Center of Excellence (CCOE)
Organizations need a dedicated team to assess scope, coordinate cryptographic policies, and provide expertise across development teams. This center becomes the command hub for a multi-year transformation program requiring cross-functional coordination.
2. Build a Comprehensive Cryptographic Inventory
This is the foundation of everything else. Organizations must construct an inventory documenting every cryptographic algorithm in use across the enterprise. This inventory must identify:
- What cryptographic algorithms are deployed
- Where they're being used (applications, systems, hardware)
- Which certificates and keys exist and where they're stored
- Key lengths, algorithm types, and certificate lifecycles
- Dependencies between systems and cryptographic implementations
- Vendor products that embed cryptography
Without this visibility, organizations cannot scope the impact of migration, prioritize risk remediation, or create realistic timelines.
3. Develop Clear Policies and Governance
Organizations need formal policies governing algorithm substitution, data retention aligned with quantum timelines, and the mechanics of cryptographic migration. This policy framework reduces confusion, eliminates arbitrary decisions, and increases manageability as organizations navigate the complex transition.
4. Implement Crypto-Agile Development Practices
Applications must be designed for cryptographic flexibility, enabling organizations to swap algorithms without massive re-engineering efforts. Organizations should test new post-quantum algorithms to understand their performance characteristics—which differ significantly from classical cryptography in key sizes, signature sizes, and computational requirements.
5. Start Immediately—No More Waiting
Organizations cannot afford to delay. Given that the average PQC migration is estimated to take years for mid-sized organizations, waiting even another year puts companies on a collision course with the 2029 deadline. Federal mandates are already in motion, with CISA requiring agencies to inventory cryptographic systems and plan automated discovery tool adoption.
What is the Cryptographic Inventory Problem for PQC Readiness? Why Are Most Organizations Stuck?
Here's where the reality hits: The entire framework hinges on that second step—building a comprehensive cryptographic inventory. Yet this is precisely where most organizations stall.
The challenge isn't just technical complexity, though that's substantial. The real obstacle is that cryptographic objects are distributed across:
- PKI infrastructure: Certificate authorities, registration authorities, validation services
- Identity systems: Authentication mechanisms, SSO implementations, federation protocols
- Application layer: Embedded cryptography in custom and commercial software
- Network layer: VPN concentrators, load balancers, API gateways
- Endpoint devices: Laptops, servers, IoT devices, mobile devices
- Cloud environments: Multi-cloud cryptographic implementations and key management services
- Machine identities: Service accounts, API keys, SSH keys, code signing certificates
Traditional discovery tools struggle because cryptography is woven throughout the entire digital fabric of modern enterprises. Point solutions that scan networks miss embedded cryptography. Application security tools that examine code don't see infrastructure-level certificates. PKI management platforms don't extend to application-layer cryptographic libraries.
What organizations need is unified visibility that spans human identities, machine identities, and the cryptographic credentials that secure them all. This is where Axiad Mesh fundamentally changes the equation.
How Can Axiad Mesh Accelerate PQC Readiness?
Axiad Mesh was built to solve the inventory problem that analysts identify as a critical step in PQC migration. As an Identity Visibility and Intelligence Platform (IVIP), Axiad Mesh provides the comprehensive cryptographic inventory that organizations need to move quickly on PQC readiness.
Unified Cryptographic Discovery Across Your Entire Identity Infrastructure
Axiad Mesh doesn't just discover identities, it discovers and inventories the cryptographic assets associated with those identities across your organization:
- Certificate discovery across PKI infrastructure: Axiad Mesh provides visibility into X.509 certificates across traditional PKI systems, cloud-based certificate authorities, and hybrid environments. This includes digital certificates for users, devices, applications, and services.
- Machine identity cryptography inventory: Axiad Mesh delivers critical visibility into API keys, service account credentials, SSH keys, and the cryptographic methods securing machine-to-machine communications.
- Integration with existing identity systems: Rather than requiring rip-and-replace, Axiad Mesh integrates with existing identity providers, access management systems, and asset management systems to create a unified cryptographic inventory without disrupting operations.
Automated Discovery at Enterprise Scale
Manual cryptographic inventories are both time-consuming and incomplete. Axiad Mesh automates discovery, continuously scanning your environment to identify:
- Certificate types, key lengths, and signature algorithms
- Certificate lifecycles, expiration dates, and renewal status
- Issuing authorities and certificate chains
- Weak cryptography that requires prioritized remediation
- Orphaned or unused cryptographic credentials
- Dependencies and relationships between identities and certificates
This automation dramatically compresses the timeline for creating Gartner's recommended inventory. Where manual efforts might take months or years, Axiad Mesh delivers comprehensive visibility in weeks.
Risk-Based Prioritization for PQC Migration
Not all cryptographic implementations pose equal risk. Axiad Mesh applies AI/ML-powered analytics to assess and prioritize cryptographic vulnerabilities based on:
- Algorithm weakness: Identifying RSA, ECC, and other quantum-vulnerable algorithms
- Key strength: Flagging certificates with insufficient key lengths
- Certificate lifecycle risk: Highlighting certificates nearing expiration that should be renewed with quantum-safe alternatives
- Identity criticality: Prioritizing high-privilege accounts and critical machine identities
- Data sensitivity: Focusing on cryptography protecting sensitive or long-lived data
This risk intelligence enables organizations to make informed decisions about migration sequencing, focusing resources where quantum threats pose the greatest danger.
Real-Time Visibility and Continuous Monitoring
PQC migration isn't a one-time project—it's a multi-year transformation requiring continuous visibility. Axiad Mesh provides real-time monitoring and alerts, ensuring that as new systems come online, new certificates are issued, or cryptographic configurations change, your inventory remains current and complete.
This ongoing visibility is essential for a crypto-agile approach, enabling organizations to track migration progress, identify new quantum-vulnerable cryptography as it's introduced, and maintain comprehensive oversight throughout the transition.
Bridging Identity and Cryptography
Here's what makes Axiad Mesh unique: it understands that cryptographic credentials don't exist in isolation—they're intrinsically linked to identities. A certificate belongs to a user, a device, or a service. An API key authenticates a specific application. An open source library is part of an application and was used by a developer. Understanding these relationships is critical for:
- Impact analysis: Determining which users and systems are affected by cryptographic vulnerabilities
- Ownership attribution: Identifying who's responsible for remediating specific cryptographic issues
- Dependency mapping: Understanding how cryptographic changes will ripple through interconnected systems
- Coordinated migration: Ensuring that identity lifecycle events (user departures, role changes) trigger appropriate cryptographic credential updates
By correlating identity data with cryptographic inventories, Axiad Mesh provides the contextual intelligence that transforms raw discovery data into actionable migration roadmaps.
The Cost of Delay Is Exponential
The Gartner article compares PQC migration to Y2K, but the analogy understates the challenge. Y2K had a fixed deadline and a known problem (two-digit year fields). PQC migration faces:
- Uncertainty about the quantum timeline: Breakthroughs could accelerate the threat
- No drop-in replacements: New algorithms have different performance profiles
- Vendor unpreparedness: Most vendors haven't prioritized PQC upgrades
- Legacy system constraints: Embedded systems and hardware may require replacement, not just updates
Organizations that begin comprehensive cryptographic discovery today give themselves 4-9 years for migration. Those who delay another year or two may find themselves attempting a decade-long migration in just 2-3 years—a recipe for incomplete transitions, security gaps, and operational disruptions.
What is the Axiad Mesh Difference? Speed Meets Comprehensiveness
What sets Axiad Mesh apart in the PQC readiness landscape is the combination of:
- Breadth of coverage: From human identities to machine identities to cryptographic credentials, all in one platform
- Depth of insight: Not just discovering what exists, but understanding relationships, risks, and priorities
- Speed of deployment: Weeks to comprehensive visibility, not months or years
- Continuity of operation: No rip-and-replace; Axiad Mesh integrates with existing infrastructure
For organizations facing the 2029 deadline, Axiad Mesh compresses the timeline for the most critical and time-consuming phase of PQC readiness: understanding what you have and where it is.
Start Your PQC Journey with Clarity, Not Confusion
The message is clear: the quantum threat is real, the timeline is short, and organizations must begin transitioning to post-quantum cryptography immediately.
But you can't migrate what you can't see. Axiad Mesh transforms daunting PQC migration recommendations into an achievable roadmap by solving the foundational challenge of cryptographic visibility. With automated discovery, AI-powered risk assessment, and unified identity-cryptographic correlation, Axiad Mesh enables organizations to:
- Build their cryptographic inventory in weeks, not years
- Prioritize quantum-vulnerable systems based on actual risk
- Track migration progress with real-time visibility
- Meet federal mandates for automated cryptographic discovery
- Establish the foundation for long-term crypto-agility
The quantum era is coming. The question isn't whether your organization needs to prepare—it's whether you'll have the visibility necessary to prepare effectively.
Learn More About Axiad Mesh for PQC Readiness
Ready to accelerate your post-quantum cryptography readiness with the visibility and intelligence you need? Axiad Mesh provides the comprehensive identity and cryptographic discovery capabilities that Gartner identifies as essential for PQC migration success.
Contact us today to learn how Axiad Mesh can help your organization build the cryptographic inventory foundation for a quantum-safe future: www.axiad.com/contact
Explore Axiad Mesh: Discover how the original Identity Visibility and Intelligence Platform extends to cryptographic discovery and PQC readiness: www.axiad.com/axiad-mesh
******************
Additional Resources
Gartner Public Article: "Post-Quantum Cryptography Is a Must to Protect Your Systems" - Available at gartner.com/en/articles/post-quantum-cryptography (Published July 22, 2025)
CISA: "Strategy for Migrating to Automated Post-Quantum Cryptography Discovery and Inventory Tools" (September 2024)
NIST: Post-Quantum Cryptography Standardization (ongoing)


























%201.avif)







