It’s a watershed moment for an industry when multiple industry analysts start writing about a new product category. First Gartner® defined the new Identity Visibility and Intelligence Platform (IVIP) category, then KuppingerCole® advised that IVIP should evolve further to Identity Visibility and Observability Platform (IVOP), and other analysts are immediately including some variation of this new category in related reports. Industry analysts have recognized what security leaders have been struggling with for years: IAM infrastructure suffers from critical visibility gaps, and this lack of transparency creates security vulnerabilities that attackers are actively exploiting.
At Axiad, we saw this problem coming. That's precisely why we launched Axiad Mesh back in 2024. Back then it didn’t have category name but it was purpose-built to provide Identity Visibility, Intelligence, and Observability.
What Problem is IVIP Addressing?
An IVIP reduces the IAM attack surface using visibility, observability, and remediation. Every CISO and IAM leader struggles with disconnected identity systems spread across numerous tools and departments, resulting in security blind spots that leave the identity attack surface largely unmonitored.
The scope of this problem is staggering.
- Decentralized IAM implementation decisions happen without adequate security oversight, resulting in serious security weaknesses including compromised machine credentials, authentication controls that have been turned off, and user accounts that should have been deleted
- Organizations struggle to evaluate identity security vendors because the market has become overcrowded with overlapping solutions focused on different aspects of IAM security, making it difficult to determine which approach best fits their needs
- Legacy IAM platforms were designed for simpler environments and cannot adequately address questions about access rights spanning modern cloud platforms, software-as-a-service applications, traditional on-premises systems, and hybrid architectures
Perhaps most tellingly, analysts forecast that within three years, nearly three-quarters of chief information security officers will adopt an Identity Visibility and Intelligence Platforms as a critical tool for reducing their organization's exposure to identity-based attacks such as stolen credentials, compromised accounts, hijacked sessions, and improper access.
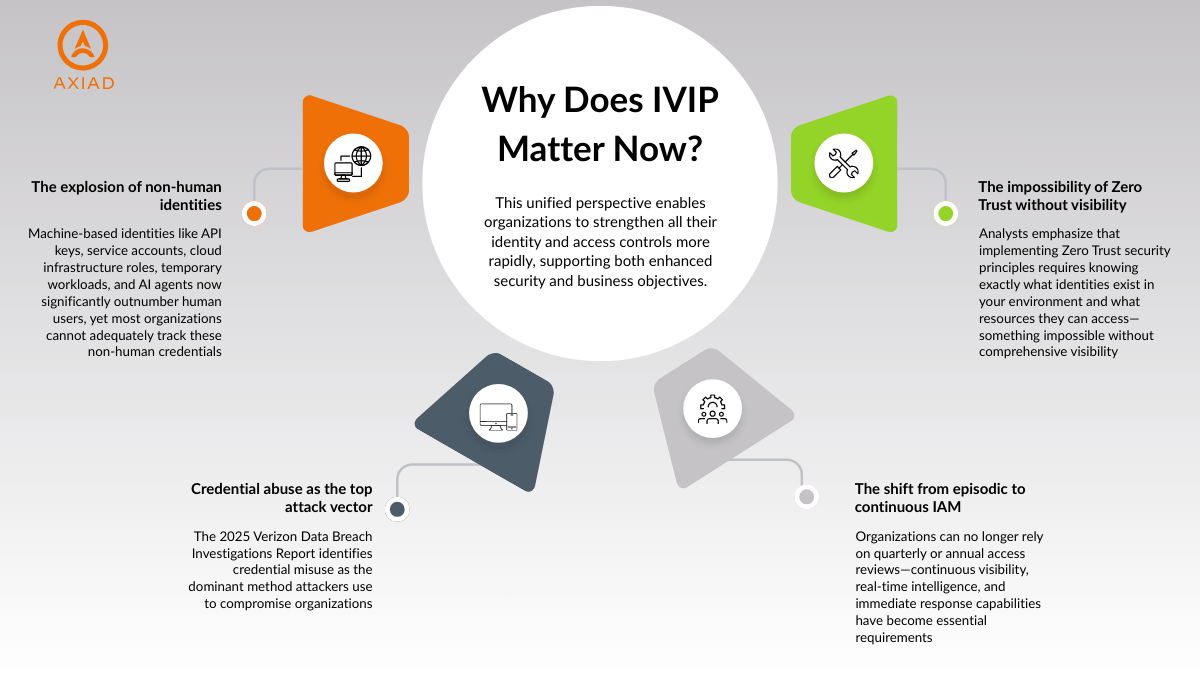
Why does this category matter now?
Research defines IVIPs as solutions that quickly integrate and consolidate IAM-related information from across the enterprise, combining this data with sophisticated analytical capabilities—often powered by artificial intelligence—to create a comprehensive view of identity information, user activities, access relationships, system configurations, and overall security posture. This unified perspective enables organizations to strengthen all their identity and access controls more rapidly, supporting both enhanced security and business objectives.
The emergence of this category addresses several converging forces:
- The explosion of non-human identities: Machine-based identities like API keys, service accounts, cloud infrastructure roles, temporary workloads, and AI agents now significantly outnumber human users, yet most organizations cannot adequately track these non-human credentials
- Credential abuse as the top attack vector: The 2025 Verizon Data Breach Investigations Report identifies credential misuse as the dominant method attackers use to compromise organizations
- The shift from episodic to continuous IAM: Organizations can no longer rely on quarterly or annual access reviews—continuous visibility, real-time intelligence, and immediate response capabilities have become essential requirements
- The impossibility of Zero Trust without visibility: Analysts emphasize that implementing Zero Trust security principles requires knowing exactly what identities exist in your environment and what resources they can access—something impossible without comprehensive visibility
Why is Axiad Mesh the original IVIP?
While the formal establishment of IVIP as a distinct category by industry analysts represents a significant milestone, the underlying problem has existed for years. At Axiad, we recognized that organizations were being overwhelmed by identity complexity—unable to achieve unified visibility across human identities in multiple identity providers (IdPs) in disparate access management systems (IAMs) as well as non-human identities across a fragmented PKI infrastructure with multiple certificate authorities and credential management operating in isolation.
That's why we built Axiad Mesh.
Launched in 2024, Axiad Mesh was specifically engineered to deliver the comprehensive identity visibility and intelligence capabilities that industry analysts now identify as essential. Our platform provides:
Unified Identity Discovery and Visibility
Axiad Mesh consolidates and correlates identity information across your complete IAM infrastructure. Rather than functioning as a replacement for existing IAM, it operates as an intelligence layer that through integrations exposes the access and permission relationships throughout your organization, covering both human and non-human identities.
Advanced Analytics and Intelligence
By applying artificial intelligence and machine learning technologies, Axiad Mesh delivers continuous risk assessment and actionable security insights that enable teams to discover and resolve identity problems before they escalate into security breaches. Our platform transcends simple data presentation—it correlates disparate identities, provides context, prioritization, and clear guidance on what requires attention and the underlying reasons.
Attack Surface Reduction
Through comprehensive visibility into identity security weaknesses—encompassing accounts that are overprivileged, orphaned, or unused, identities without proper ownership, authentication controls that are missing or have been disabled, exposed authentication credentials, and identities with poor cryptography levels—Axiad Mesh enables organizations to systematically reduce their IAM attack surface with measurable results over time. This approach aligns directly with Gartner's emphasis on outcome-driven metrics for demonstrating concrete security improvements.
Remediation and Orchestration
Moving beyond passive visibility, Axiad Mesh will incorporate automated remediation functions and workflow orchestration to empowers security operations teams to address identity hygiene gaps fast as they emerge, rather than waiting weeks or months for scheduled access review cycles.
When should organizations adopt IVIP?
Industry research makes clear that even organizations with sophisticated IAM programs continue to face significant visibility challenges. Despite substantial investments in identity technologies, security blind spots remain pervasive, and organizations can only address identity security weaknesses and reduce their exposure by achieving comprehensive visibility across both integrated and standalone identity systems.
Organizations that delay adoption while waiting for mainstream market acceptance will continue operating with critical visibility gaps that threat actors are exploiting right now. Early adopters who implement IVIP capabilities today will gain years of incremental security improvements and operational intelligence over late adopters.
What should IAM leaders do to adopt IVIP?
Industry analysts recommend that IAM leaders:
- Build a foundation of unified visibility by creating comprehensive oversight across all identity systems, whether they are centrally managed or operating independently
- Empower security operations teams with visual representations of user and machine identities, access permissions, authentication and cryptography levels, associated risks, and prioritized remediation actions to eliminate uncertainty in distributed IAM environments
- Establish continuous improvement practices using visibility data and automated remediation capabilities to systematically address security gaps and demonstrably reduce identity-related risk over time
This strategic approach describes exactly what Axiad Mesh was purpose-built to accomplish.
Is Axiad Mesh an IVIP?
The formal establishment of the IVIP category confirms what we've understood and worked toward since Axiad Mesh's inception: effective security and governance with comprehensive visibility as their foundation. Organizations cannot adequately reduce risks they cannot observe.
The new IVIP category serves as a clear message to the identity security industry: visibility capabilities can no longer be treated as secondary features embedded within traditional IAM products. They represent a critical, dedicated function that organizations must prioritize to defend against contemporary identity-focused attack methods.
At Axiad, we're proud to have anticipated this industry shift and delivered a production-ready solution that organizations can implement immediately.
Is now the time to act on IVIP?
With stolen credentials representing the most prevalent attack method, machine identities multiplying at exponential rates, and regulatory requirements intensifying (including SEC cybersecurity disclosure mandates and the EU's Digital Operational Resilience Act), the strategic question has shifted. It's no longer whether your organization requires identity visibility and intelligence capabilities—it's whether you can afford the disadvantage of delaying.
Industry analysis indicates that most security executives will adopt IVIP solutions within the next three years. Organizations that act decisively now will invest the coming years in continuous security posture improvement, systematic remediation of identity hygiene issues, and measurable reduction of their identity attack surface. Those who postpone action will spend the same period operating without adequate visibility, depending on fragmented legacy tools and hoping their incomplete security coverage proves sufficient against the next threat actor.
Learn more about Axiad Mesh
Axiad Mesh brings more than a year of operational deployment experience addressing the precise challenges the industry experts have now formalized. As the original IVIP solution, Mesh was specifically engineered to provide organizations with comprehensive identity visibility, sophisticated intelligence capabilities powered by advanced analytics, and quantified risk scores necessary to prioritized remediations to secure complex, hybrid identity infrastructures.
Whether your organization is grappling with human or non-human identities, Axiad Mesh delivers the transparency and control essential for modern identity security.
Learn more at https://www.axiad.com/axiad-mesh


























%201.avif)







